What Makes a Blockchain: Protocols and the Future
In previous blog posts, we’ve discussed some promising uses of blockchain technology including financial services, identity management, and pharmaceutical companies. Since new opportunities are emerging at a rapid rate, it is imperative to have a full understanding of blockchain technology.
Now, we will look into what exactly makes a blockchain a ‘blockchain’ – right down to the basics.
This blog post will explain some of the fundamental protocols that are in place, as well as other powerful protocols.
Blockchain’s Humble Beginning: Bitcoin
The (idea of a) blockchain began as the brainchild of Satoshi Nakamoto in his (or her) 2008 paper: Bitcoin: A Peer-to-Peer Electronic Cash System.
However, Satoshi Nakamoto wasn’t the first to create an electronic cash system. Dating back to the 1980s, electronic cash systems have existed. From David Chaum’s Digicash (one of his protocols will be discussed below), to the more famous example of PayPal.
Satoshi engineered Bitcoin to be a peer-to-peer electronic cash system that enabled parties to initiate transactions while bypassing the current Bourgeois infrastructure.
Blind Signature
The Blind Signature or Chaumian blinding is a safety protocol that helps users in a blockchain maintain complete anonymity. This is accomplished by using private/public Elliptic Curve Digital Signature Algorithm (ECDSA) keys.
To explain blind signatures we can use the following analogy:
A voter encloses his ballot in an envelope that is lined with a special carbon paper. This envelope also contains all the voter’s credentials in a pre-printed format. The ballot is marked through the carbon paper and afterwards an official verifies the credentials and signs it. The voter can now place the signed envelope in a normal envelope. The ballot’s content is not compromised because the signer had no way of seeing it.
A blind signature allows for anonymity in a very traditional fashion, and these signatures are secured with the content always privately available to the user. The protocol allows for digital cash to be processed with no need for identity compromisation.
The goal for digital cash was to become as anonymous as the traditional form of cash. When you withdraw cash out of a bank, the bank does not question what you are using it for. When you pay for a service, the merchant does not have to know who you are. These two factors provide you with anonymity. In an online transaction, not only does a bank have to know what you’re buying, the merchant also needs to know who you are. This has alarming potential for an invasion of privacy to occur.
Bitcoin uses public keys so it won’t expose your identity. You sign the transaction with your public key and everything is cleared, which provides users with a high degree of anonymity. This quality was revered by all users who initially heard about Bitcoin. Anonymity incentivized the movement towards cryptocurrencies and, most importantly, blockchains.
Proof-of-Work Explained
Bitcoin, namely Satoshi, provided solutions for double-spending with a number of already-popular protocols that mostly date back to the 80’s. Digital signatures, hashing, Merkle trees, and verification methods created a system called “Proof-of-Work”, also known today as the “Nakamoto Consensus”.
Proof-of-Work is the Bitcoin system used to verify and legitimize transactions before they are placed on the Bitcoin blockchain. A Proof-of-Work is a “riddle” that is very difficult to generate but easy to verify.
How is This Done?
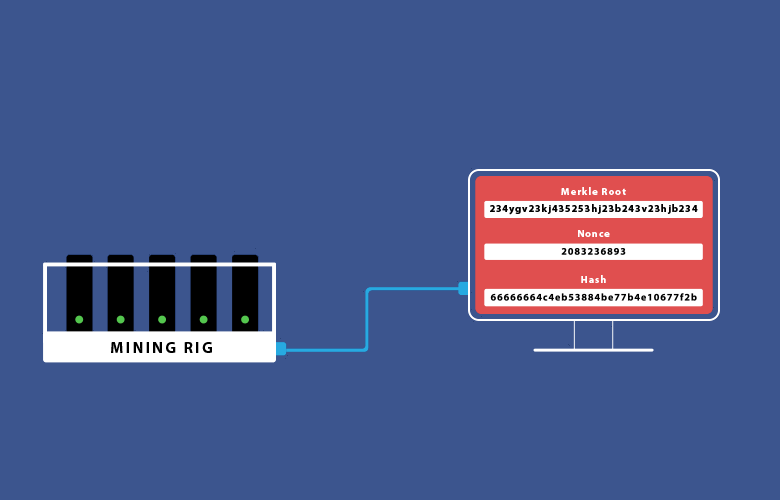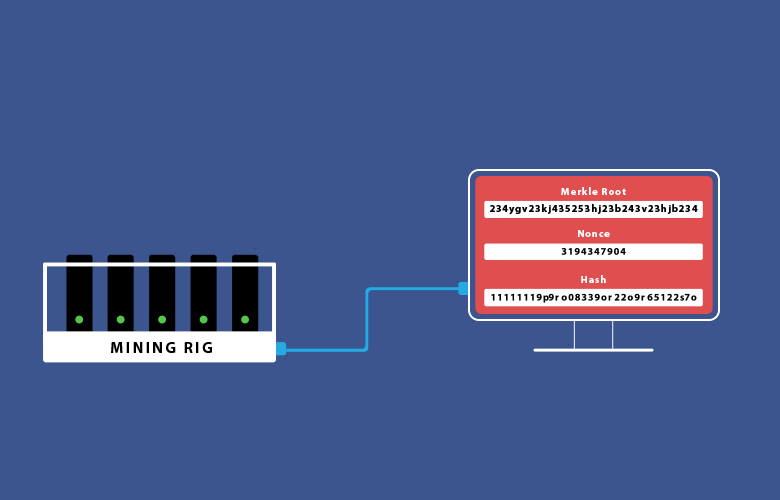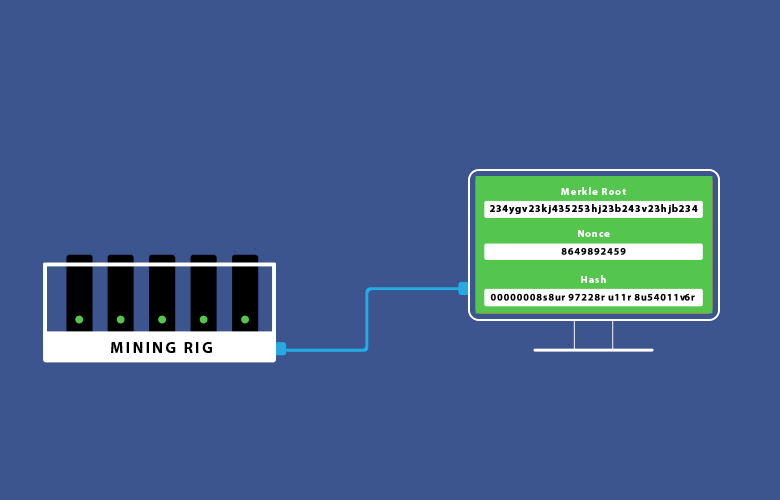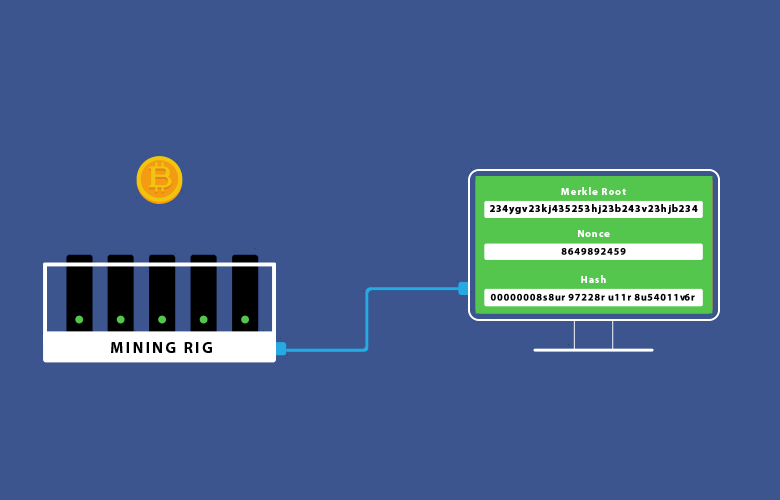
The Bitcoin network generates a block approximately every 10 minutes. These blocks contain the transactions that miners decide to include. Each transaction contains specific data – inputs and outputs, version bits, lock times, etc.
The group of transactions that make it inside the block are then hashed in a Merkle tree to create a Merkle root. This final root is the main “ingredient” that is transmitted to miners in order to begin using their computational powers for the hashing process.
The hashing is a literal guessing game that is done through the use of a message (Merkle root) and a nonce. A nonce is a randomly generated number that when hashed with the message will generate a finite amount of starting zeros (depending on the difficulty) in the final hash. When a miner guesses the correct nonce, fulfilling the condition of starting zeroes, the block is correctly mined, rewarding the miner. The word “guess” is being used simply because the correct nonce is found out of pure luck (and computational power).
Finally, the guessed nonce is advertised to all other nodes in the network, letting them know that the block was solved, and now requires verification. The nodes complete the verification process using the advertised nonce to hash the Merkle root. This is the easy part, they get the Merkle root that is already available to everyone, hash it with the miner’s nonce, and confirm that this is the correct solution.
Double-Spending Issue
Just like any other system, Proof-of-Work has its flaws. Although it is very difficult, the Proof-of-Work process can be manipulated. Some methods that can abuse the system’s issues are:
-
Race Attack – Two transactions that conflict with one another are sent in rapid succession, e.g:
- The attacker then places another payment using the same bitcoin addresses in another transaction that the blockchain did accept.
- Finney Attack– Named after Hal Finney, this method is more sophisticated than a race attack.
The attacker begins mining a block, adding a transaction that sends some coins back to him but doesn’t broadcast that transaction. - After the attacker finds the block nonce, he/she doesn’t broadcast it. Instead, he/she send the same amount of bitcoin to a merchant for an exchange of goods and services.
- If the merchant accepts the payment, providing an irreversible service, the attacker will continue to broadcast his first transaction that sends the coins back to him, overriding the transaction to the merchant.
This form of attack can be mitigated if you wait for 1-6 blocks to be confirmed (depending on the size of the transaction).
- 51% Attack – The only major form of attack that could bring down the entire Bitcoin network is the 51% attack. A 51% attack could be facilitated maliciously by miners or by network operators purposefully splitting the mining network. First, miners would need to take control of the major hashrate. Next, they would generate a private blockchain (also called a private fork of the main-chain), eventually catching up with the current public blockchain. From here they could fork the current blockchain with their own private blockchain and it would be completely unpreventable. Although this would be extremely costly, it is still a possibility. However, several game theoretic attack scenarios have been proposed which can reduce the cost considerably.
Although the PoW is very safe, it is still not 100% safe. The aforementioned methods are all feasible, and some have already been actively attempted by some attackers.
Bitcoin’s Current Blockchain Issue: Scalability
Although Bitcoin has proven itself to be the highest-valued, most used cryptocurrency currently in the market, it does have issues that prevent it from fulfilling its full potential. These issues are mostly tied to the scalability of its blockchain, the transaction rate, confirmation time, etc. However, one can also argue that its commodity-like nature and price fluctuations are also a major issue for large scale adoption.
Imagine you had to download a digital drive of EVERY song just to listen to one song online. Sounds crazy, right? In order to provide traits such as immutability and decentralization, Bitcoin forces its users do just that.
To enter the Bitcoin mining process you must download the entire Bitcoin blockchain. This blockchain consists of blocks chained to one another to create a ledger that can be traced back to its genesis block. Each block size is a maximum of 1 Megabyte, this means that transactions per block, or in other words transaction throughput, is limited as well.
Although 1 MB is quite low, keep in mind that it takes a small amount of time to generate a new block as well. This generation process began in 2008, and as of July 2017 almost 480000 blocks had already been generated. The ledger size added up over the years, thanks to the staggering 127 Gigabytes of transaction data (as of July 2017).
Bitcoin has a very low transaction rate because of its block size limit (1 MB). This means that no matter how many transactions take place, as soon as their total size adds up to 1 MB, the blockchain will not accept the next transaction into the current block, placing it on hold until the next block. These transactions also take a minimum of 10 minutes to confirm because a new block is generated roughly every 10 minutes. At this current stage, it’s nowhere close to competing with Visa’s maximum of 56,000 tps as a pure payment network.
To recap, Bitcoin’s blockchain size and low tps are the major issues that prevent mass scalability of the technology. The following paragraphs will explore a few possible avenues to solve the scalability issues that all blockchain technology is experiencing, not just Bitcoin.
Protocols Bring Hope
In the digital world, protocols are sets of rules that determine how devices transmit data to one another. Protocols are defined as stateless, meaning their current action should not depend on what happened in a past action (meaning there is no long-term memory). Blockchains don’t fulfill this narrow definition of protocols as they are stateful.
The global Bitcoin community has fervently tried to advance blockchain tech for years, coming up with ingenious ideas, which will be explained below. These protocols aim to make blockchains faster, more scalable, more accessible, and offer better security.
IPFS (InterPlanetary File System)
IPFS is a peer-to-peer hypermedia protocol that is currently aiming to augment or replace HTTP. HTTP is an old application-layer protocol built with a Channel Based Networking paradigm in mind. HTTP uses a request-response model. IPFS is instead based on the Content Centric Networking (CCN) principle which has been proposed since the 70s, and aims to create a more effective network through the following:
- Efficient use of bandwidth – HTTP uses a single server to get the files to a client. This means that a large amount of bandwidth is wasted from the back-and-forth communication. IPFS allows the client to request files and have them sent back from the nearest possible sources (multiple at a time), saving time and bandwidth. IPFS also removes duplicate files, because each file is uniquely hashed in the system.
- Better versioning – Think Git. IPFS provides methods for people to version, mirror, and save data using better techniques than currently present in the Bitcoin blockchain./li>
- Decentralization – Although the internet was planned as a decentralized network for primarily military purposes, it slowly started to become more and more centralized for economic reasons. IPFS provides a more decentralized version of the Internet; going back to the roots./li>
- Backboneless – If a major ISP were to go offline suddenly it would be devastating for the current system, but IPFS local nodes could still fetch data from one another without needing a global backbone.
IPFS does this by generating a unique hash for every file that goes inside blocks. It removes duplicate files and tracks the history of the files. All the participants store only what they care to store and use a form of indexing to help other participants in the network understand who is storing what. When a person wants to lookup a file, they simply use the IPNS (InterPlanetary Naming System), which is a naming system designed for human-readability, and look it up with a file name.
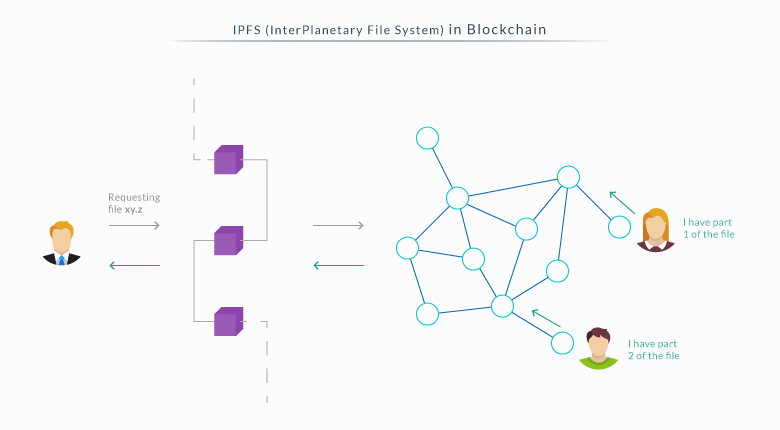
This protocol is very promising, especially in collaboration with blockchains. IPFS would allow blockchains to store large amounts of data and place immutable IPFS links inside the blockchain, instead of having to place the whole transaction data; saving size and lowering latency.
Matrix
The Matrix (not the movie) is a communications protocol that allows for real-time communication. This protocol attempts to address the issue of IP communications fragmentation by creating a model for a private communication backbone. The Matrix provides HTTP APIs to make it easier for developers to integrate it into their system. This allows for communication from different environments through a single Matrix account, making it a very viable option for communicating.
The Matrix’s main goal is syncing data and messaging for the web. This would allow users to communicate with ease between different channels and still have a log of the entire chat history. This protocol isn’t just for exchanging messages, it can also be used for exchanging all sorts of data.
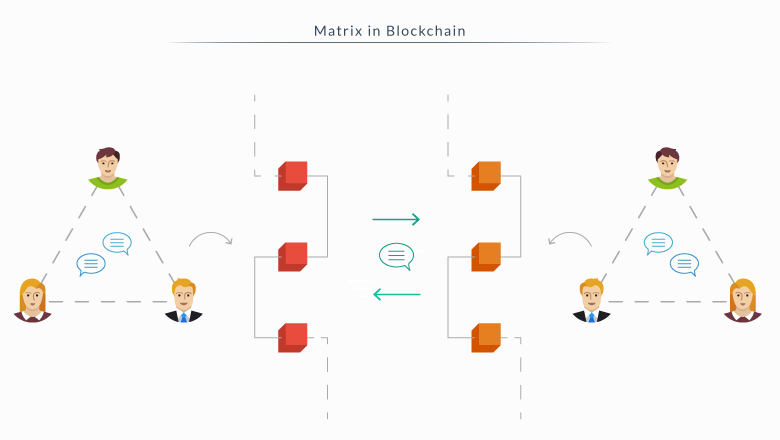
Bitcoin can use this protocol in order to communicate with other private blockchains, exchanging data in a very reliable and safe ecosystem.
QUIC (Quick UDP Internet Connections)
QUIC is an experimental transport layer protocol that was created by a Google employee in an attempt to fix some of the connection issues on the internet. Its main goal is to support multiplexed connections over UDP. QUIC uses techniques such as bandwidth estimation and pacing packet transmissions to avoid congestions and packet loss.
Although Google had already developed another protocol for this – SPDY – its biggest drawback is that it’s a TCP protocol. During a TCP transmission, if a single packet is lost then the entirety of multiplexed connections are stalled. With UDP and QUIC, only a single multiplexed connection is stalled if a packet is lost, making it an amazing protocol to save bandwidth
QUIC provides two features:
- Lower latency – QUIC doesn’t use a lot of round trip times (RTT), unlike TCP which engages in a three-way handshake before it establishes a connection (which is connected to point two). QUIC servers provide users with a static configuration record which the client will store as a synchronized cookie making the next future connection much faster.
- Reflection attacks are impossible – Reflection attacks use the same protocol in both directions. For example, an attacker would spoof the victim’s IP address and would send requests to a UDP server and flood the victim with packets.
Since the size of UDP reflection attacks have been slowly increasing since 2010, QUIC has taken an approach in an attempt to stop it. Although TCP has the three-way handshake which made reflection attacks impossible, that opened the gates for a “SYN” attack. An attacker could initiate thousands of connections and flood the server with open connections, disabling the connection users that want to connect.
QUIC has taken a different approach; sending all session negotiation information in the first initial packet, which makes a reflection attack too costly for an attacker. This also reduces latency for a connection because you do not have to engage in a three-way handshake each time a session is opened.
QUIC could operate inside the transport layer protocol. This protocol is responsible for connecting blockchains and nodes, seeing as QUIC is a secure and reliable UDP protocol for content addressable networks(CANs).
The Lightning Network
The biggest issue with the Bitcoin blockchain is its scalability. The following protocol is one of the most promising that we have so far. What does The Lightning Network aim to solve exactly?
- Transactions per second issue – Bitcoin was limited to a slow 7 transactions per second, prior to SegWit implementation, which is quite low if it wants to scale globally.
- Confirmation times – A block takes ten minutes to generate which means that transactions requiring a confirmation will have to wait ten minutes.
- Microtransactions – Bitcoin charges users a fee which cripples microtransactions completely. This fee runs from five to ten cents. Although that may sound cheap, it is actually expensive in regards to a transaction that small.
The Lightning Network relies on payment channels to solve these issues. A payment channel is a two-party channel that creates a multi-signature transaction between the participants. After the creation of a channel, entities can participate in the transactions, which are made valid when both keys of the party members sign the contract.
Inside the blockchain each transaction is broadcast as soon as it is completed. Inside a payment channel a transaction is transmitted only when both parties decide to end the channel because they’re done exchanging. The last transaction is transmitted, which includes the total amount of all the transactions that occurred.
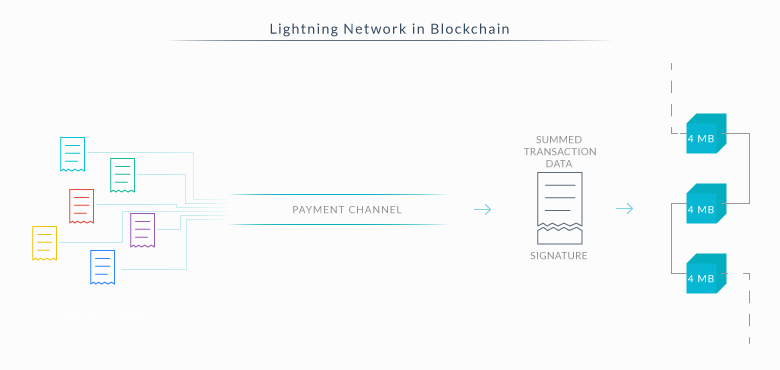
If we were to send funds to another party, we wouldn’t have to worry about the nodes who helped transport the amount because the Lightning Network also removes the risks of attack through the use of smart contracts. A third person participating in the channel would not receive his money until he has forwarded them to the destined party.
The Lightning Network uses a “hashed time lock contract” to ensure that if the man-in-the-middle goes offline, the sending party will get a full refund of the amount, ensuring the safety of the transaction.This protocol also relies on spotting older transactions in the blockchain that might be used as an attack. If a malicious party wants to broadcast an older transaction, the Lightning Network will detect that broadcast and automatically penalize that entity, ensuring that the transaction is safe.
The Lightning Network is one of the protocols with the biggest potential to change Bitcoin’s blockchain (and blockchains globally) and revolutionize its scalability and speed issues.
For more about SegWit and Lightning Network, you can go to one of our previous blogs.
Protocols Mitigate Risk
Although an overhaul of Bitcoin could (theoretically) be done, the results could prove to be disastrous due to the security flaws that might appear. It’s the same as QUIC being used as a protocol instead of “just fixing TCP”. TCP is built in an opefrating system kernel making the transitional time marginally slower than a simple application layer protocol like QUIC.
Protocols can augment existing systems with greater ease than having to perform a complete system overhaul, this allows for incredible flexibility. Through the use of different protocols we are sure to see all blockchains, not just Bitcoin, evolve to their maximum boundaries.